Real World Web Application Security Testing
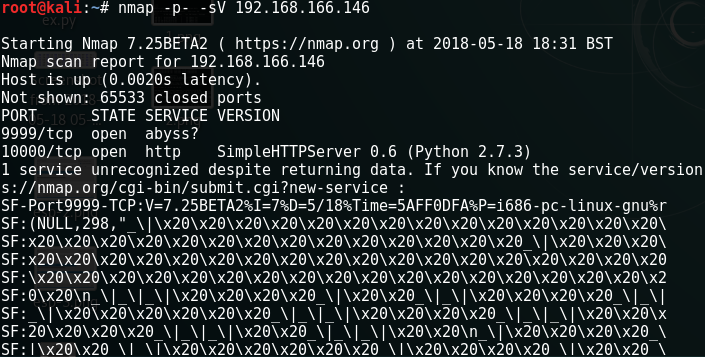
Introduction Web application security testing in the real world rarely provides opportunities for getting a reverse shell and ultimately “rooting the box” as is our usual goal in CTF scenarios. Nevertheless, it is very rare to find web applications with no significant vulnerabilities, and in my experience it’s nearly always possible to gain access to information and functions that are supposed to be restricted, often by getting access to the administrator account or equivalent. In this post, I’ll walk you through the tried and tested techniques I’ve employed over many years to achieve consistently good results. And before we get started, if you’ve ever read a web application pentest report you’ll most likely be very familiar with the many low-rated vulnerabilities that seemingly every site suffers from: Overly permissive CORS policy, secure flag not set on cookie, no anti-CSRF tokens, weak SSL ciphers supported etc. etc., the list goes on. I’m not going to talk about these types of i